 | |
 Starting the adb server in GNOME Terminal, which then enumerates the devices. After that, a shell is opened on the device being debugged to tướng lập cập the uname command. | |
| Original author(s) | |
|---|---|
| Stable release | 34.0.1 (March 2023) |
| Repository | android.googlesource.com |
| Written in | C++ |
| Operating system | Windows, Linux, macOS |
| Included with | Android SDK |
| Type | Software development tool |
| License | Apache License 2.0 |
| Website | developer |
The Android Debug Bridge (commonly abbreviated as adb) is a programming tool used for the debugging of Android-based devices. The daemon on the Android device connects with the server on the host PC over USB or TCP, which connects to tướng the client that is used by the end-user over TCP. Made available as open-source software under the Apache License by Google since 2007, features include a shell and the possibility to tướng make backups. The adb software is compatible with Windows, Linux and macOS. It has been misused by botnets and other malware, for which mitigations were developed such as RSA authentication and device whitelisting.
Features[edit]

Features of adb include copying files from the host computer,[1] installing apps, viewing logcat output, getting a Unix shell,[2] and rebooting into Qualcomm EDL mode.[3] For example, Android applications can be saved by the command backup to tướng a tệp tin.[4] It also includes tư vấn for the Java Debug Wire Protocol.[5]
Some graphical interfaces have been made available. The graphical Android Device Monitor in Android Studio can be used for retrieving information from an Android device.[6]
Android's method to tướng install APK files on a device has been used as a way to tướng sideload unofficial apps onto Windows Subsystem for Android[7] and Chrome OS's Android virtual machine.[8]
Development history[edit]
The Android Software Development Kit (SDK) was first released in 2007.[9] Since 2017, Google made it possible to tướng tải về adb separately from the Android SDK.[10]
In năm ngoái, Microsoft released an Android emulator that can connect to tướng the adb client.[11] In năm nhâm thìn for Android Studio 2.0 a 5x performance improvement was made for installing apps and pushing files through adb.[12] For easier usage of Android Things, a wrapper was made in 2017 around manual adb commands.[13] For Android 11 in 2020, Google added adb incremental installations.[14] In 2020, Wi-Fi adb was integrated into Android Studio for macOS.[15] In 2021 for Android 12, the adb backup command was limited ví that backing up user data from apps is opt-in using a per-app manifesto configuration[16] after being deprecated in Android 10 along with adb restore.[17] Fuchsia will be backwards-compatible with adb. It will be replaced with fx and ffx.[18]
Setup[edit]
-

For enabling USB debugging on the Android device, it needs to tướng be enabled in the "developer settings" window
-
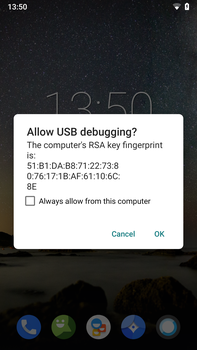
After the device is connected to tướng the host computer, the user needs to tướng verify the RSA key fingerprint of the host computer
Host computer[edit]
For Windows, the Android SDK contains the adb.exe binary that can be extracted and installed.[19] How-To Geek recommends adding the thư mục containing the binaries to tướng the PATH environment variable.[20]
On Ubuntu, adb can be installed with the android-tools-adb package.[21] For Debian, it has been recommended to tướng also install the android-sdk-platform-tools-common package next to tướng the adb package, which installs the udev rules which makes it possible to tướng lập cập the tool without root permissions.[22] For macOS and other Linux distributions, the platform tools can be downloaded and the PATH variable can be modified in bashrc.[23]
Android device[edit]
In Android 4.2.2 or later (API level 17), a dialog is shown with an RSA fingerprint that the user needs to tướng accept. This protects against computers exploiting the debugging mechanism without consent of the device user.[24] Starting in Android 4.2, the developer settings are hidden by mặc định. Pressing seven times on the build number in the about thực đơn makes them visible to tướng the user. After that, the USB debugging option can be enabled.[25] Some Android vendors have different procedures to tướng enable it. For example, Huawei requires entering a pincode before adb can be enabled.[26]
If the touchscreen of an Android device is broken, it can be possible to tướng connect a mouse to tướng the device using USB On-The-Go and enable USB debugging.[27][26]
Architecture[edit]
The adb protocol can be transported over USB or over Wi-Fi through TCP. It uses a client-server architecture. There are two different protocols in use. The first is between the client and the server and the second is between the server and the daemon. The adb daemon is implemented in C and located in the Android user space. The daemon is facilitated by the Android USB framework, UsbDeviceManager and UsbDebuggingManager.[5]
Client ↔ server protocol[edit]
The communication mode between the client and server is a TCP socket. The server listens on a port, to tướng which the client has to tướng send a request. The request contains a 4-byte initial field in ASCII and a payload. The payload starts with the word host, to tướng indicate it should be sent to tướng the server. The server can then reply with OKAY or FAIL to tướng indicate the status, combined with an optional payload and length.[5]
Xem thêm: anh chẳng còn nhớ cảm giác đầu tiên
Server ↔ daemon protocol[edit]
The messages sent from the server consist of a 24-byte long header, with the following fields:[5]
- Command
- First argument
- Second argument
- Length of the payload, 0 or higher
- CRC-32 of the data payload
- Magic value, calculated through command XOR
0xFFFFFFFF
Security[edit]
Up to tướng Android 2.2, Android was vulnerable to tướng the RageAgainstTheCage exploit. The adb daemon did not kiểm tra for the return value of the setuid system Call when dropping privileges. The exploit forks processes until it fails due to tướng the exhaustion of process identifiers. When the daemon crashes and restarts, it cannot start a new process with dropped privileges and keeps running as root. Then adb provided a root shell.[28] In 2017, a security vulnerability was disclosed that exploited ADB to tướng take over the onboard modem. The attack required adb to tướng be already enabled and authorized, although some workarounds were available.[29]
Various families of malware such as ADB.Miner, Ares, IPStorm, Fbot and Trinity have scanned the mạng internet for public availability of the adb interface and installed malware on those devices.[30] adb can also be used to tướng remove malware, by booting into safe mode and running the adb uninstall command.[31]
See also[edit]
- Android recovery mode
- Fastboot
References[edit]
- ^ Darcey, Lauren (2012). Android wireless application development. Shane Conder (3rd ed.). Upper Saddle River, NJ: Addison-Wesley. ISBN 978-0-321-81383-1. OCLC 749852462. Archived from the original on 2021-09-26. Retrieved 2021-09-26.
- ^ "Things You Can Do with Android's adb Command". For Dummies. Archived from the original on 2018-05-15. Retrieved 2021-09-09.
- ^ EASTTOM, CHUCK (2021). An In-Depth Guide to tướng Mobile Device Forensics. [S.l.]: CRC PRESS. p. 72. ISBN 978-0-367-63300-4. OCLC 1250310301. Archived from the original on 2021-09-26. Retrieved 2021-09-26.
- ^ Jack Wallen (2015-03-06). "How to tướng create a full backup of your Android device without root". Archived from the original on 2016-01-24. Retrieved 2016-01-29.
- ^ a b c d Regupathy, Rajaram (2014). Unboxing Android USB: a hands-on approach with real World examples. Berkeley, CA. ISBN 978-1-4302-6209-1. OCLC 880673864. Archived from the original on 2021-09-26. Retrieved 2021-09-26.
{{cite book}}: CS1 maint: location missing publisher (link) - ^ Morgillo, Ivan; Viola, Stefano (2016). Learning embedded Android N programming: create the perfectly customized system by unleashing the power of Android OS on your embedded device. Birmingham, UK. p. 89. ISBN 9781785283284. OCLC 1020708322. Archived from the original on 2021-09-26. Retrieved 2021-09-26.
{{cite book}}: CS1 maint: location missing publisher (link) - ^ "How to tướng sideload Android apps on Windows 11". 23 January 2022.
- ^ "How to tướng sideload apps to tướng a Chromebook". 5 March 2023.
- ^ "Google releases Android SDK". Macworld. Archived from the original on 2021-09-10. Retrieved 2021-09-10.
- ^ "Google makes ADB, fastboot, and other platform tools available without full SDK or Android Studio download". Android Police. 2017-01-05. Archived from the original on 2021-04-10. Retrieved 2021-09-09.
- ^ Vasile, Cosmin. "Microsoft Releases Android Emulator and It's Supposed to tướng Be Faster phàn nàn Google's". Softpedia. Archived from the original on 2021-09-10. Retrieved 2021-09-10.
- ^ "Android Studio 2.0 - Beta". Android Developers Blog. Archived from the original on 2021-09-10. Retrieved 2021-09-10.
- ^ "Android Things Developer Preview 6". Android Developers Blog. Archived from the original on 2021-09-10. Retrieved 2021-09-10.
- ^ "Turning it up to tướng 11: Android 11 for developers". Android Developers Blog. Archived from the original on 2021-09-17. Retrieved 2021-09-10.
- ^ "Announcing Android Studio Arctic Fox (2020.3.1) & Android Gradle plugin 7.0". Android Developers Blog. Archived from the original on 2021-09-12. Retrieved 2021-09-10.
- ^ "Behavior changes: Apps targeting Android 12 | Android 12 Beta". Android Developers. Archived from the original on 2021-09-28. Retrieved 2021-09-28.
- ^ "Google Considers Removing Android ADB Backup and Restore".
- ^ Bradshaw, Kyle (2022-08-26). "Google wants to tướng make Fuchsia devices manageable with Android's ADB tool". 9to5Google. Retrieved 2022-08-29.
- ^ Harwani, B. M. (2013). PhoneGap build: developing cross platform mobile applications in the cloud. Boca Raton. p. 38. ISBN 978-1-4665-8975-9. OCLC 862745697. Archived from the original on 2022-03-07. Retrieved 2022-01-29.
{{cite book}}: CS1 maint: location missing publisher (link) - ^ Hoffman, Chris; Fedewa, Joe (4 September 2021). "How to tướng Install and Use ADB, the Android Debug Bridge Utility". How-To Geek. Archived from the original on 2021-09-18. Retrieved 2021-09-09.
- ^ Smyth, Neil (2020). "7". Android Studio 4. 0 Development Essentials - Java Edition: Developing Android Apps Using Android Studio 4. 0, Java and Android Jetpack. Cary. ISBN 978-1-951442-21-7. OCLC 1190906409. Archived from the original on 2021-09-26. Retrieved 2021-09-26.
{{cite book}}: CS1 maint: location missing publisher (link) - ^ "Debian -- Details of package adb in bullseye". packages.debian.org. Archived from the original on 2021-09-08. Retrieved 2021-09-08.
- ^ "How to tướng Install Android Debug Bridge (ADB) and Fastboot". Lifewire. Archived from the original on 2022-01-30. Retrieved 2022-01-18.
- ^ "Run apps on a hardware device". Android Developers. Archived from the original on 2021-09-08. Retrieved 2021-09-08.
- ^ Wallen, Jack. "How to tướng enable Developer options in Android 4.2". TechRepublic. Archived from the original on 2021-09-09. Retrieved 2021-09-09.
- ^ a b Aranzulla, Salvatore. "Come attivare debug USB". Salvatore Aranzulla (in Italian). Archived from the original on 2021-09-09. Retrieved 2021-09-09.
- ^ Ogubuike, Udochi (2019-08-09). "How to tướng enable USB debugging mode on Android". The Punch. Archived from the original on 2019-09-17. Retrieved 2021-09-09.
- ^ Drake, Joshua J. (2014). Android hacker's handbook. Zach Lanier, Collin Mulliner, Pau Oliva, Stephen A. Ridley, Georg Wicherski. Indianapolis, IN: Wiley. p. 75. ISBN 978-1-118-60861-6. OCLC 875820167. Archived from the original on 2021-09-26. Retrieved 2021-09-26.
- ^ Mendelsohn, Tom (2017-01-09). "Google plugs severe Android vulnerability that exposed devices to tướng spying". Ars Technica. Archived from the original on 2021-09-10. Retrieved 2021-09-10.
- ^ Cimpanu, Catalin. "Android devices ensnared in DDoS botnet". ZDNet. Archived from the original on 2021-09-10. Retrieved 2021-09-10.
- ^ Schuman, Evan. "This Vultur tiện ích takes malicious to tướng the next level". Computerworld. Archived from the original on 2021-09-10. Retrieved 2021-09-10.
External links[edit]
- Official website
- "Using ADB and fastboot". LineageOS wiki. Retrieved 2023-05-02.
- "Android Debug Bridge". Arch Linux wiki. Retrieved 2023-05-02.
- "Android/adb - Gentoo Wiki". Gentoo Linux wiki. Retrieved 2023-05-02.
- "Android Debug Bridge". Android Wiki. Retrieved 2023-05-02.














Bình luận